Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API
From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
 Cyanite86047y@illusion466
Cyanite86047y@illusion466
You mean for the passwords shown at the begining..? No, it's a sha.
For the actual text encoding, yes, I did. That was the point of the project.
The hash at the begining is used as a seed for the generation of the encryption/decryption keys, as well as various parts of mixing and changing of the message. And even a single letter difference in the cyphered message itself or it being one character shorter or longer will fail the decryption. -
 Cyanite86046y@linuxxx
Cyanite86046y@linuxxx
If i remember correctly.. I mix (not simply combine) the password and salt. If no salt if provided, I use a default.
Each characracter in the hash is individually used for encryption, I forgot to mention that earlier. And I try not to use the hash in repetitive ways. -
 Cyanite86046y@linuxxx
Cyanite86046y@linuxxx
I just picked the project back up, cleaned up the code (a little) added UTF-16 support (from just ASCII) and moved to Python3.
I also open sourced the project. It's called "firecoder", you can find it on my github profile. -
 Cyanite86046y@linuxxx
Cyanite86046y@linuxxx
I'll try and make it so that I can encrypt binary files like images and applications soon. It seems like I can partially do it, but the encoding doesn't come out quite right. I'll work on it again soon. Probably tomorrow.
Related Rants




 No questions asked
No questions asked As a Python user and the fucking unicode mess, this is sooooo mean!
As a Python user and the fucking unicode mess, this is sooooo mean!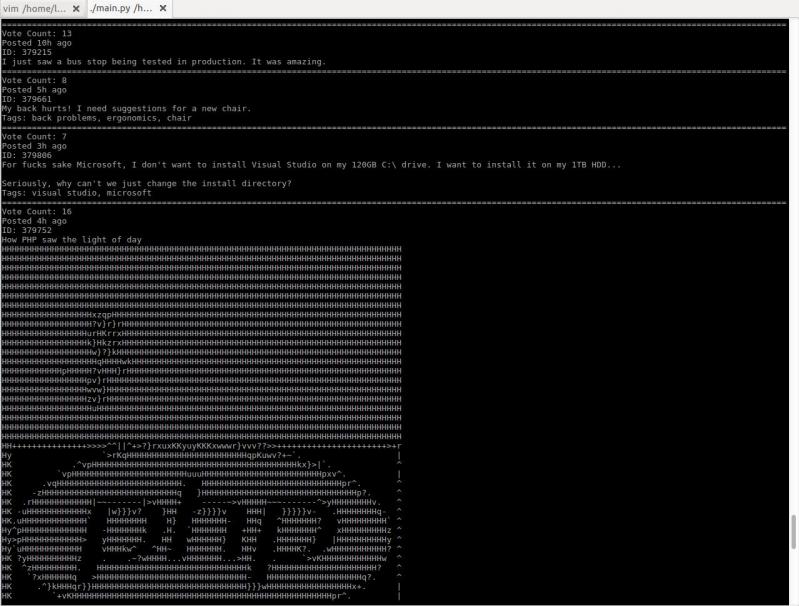 I just started working on a little project to browse devrant from terminal. It converts images to ascii art!
I just started working on a little project to browse devrant from terminal. It converts images to ascii art!
Who would be interested in reviewing an old peice of Python code I wrote..? It's a few years old, and it uses basic procedual generation to cypher text (entry, or ASCII files) using a hashed password. It's a command line tool.
I used to brag about how "secure" it was, and now I'm curious if it is secure or not.
I plan on picking it back up and open-sourcing it, but I want to know what problems might be wrong with it now.
question
code-review
python
encryption
cypher